Comparing 30 vendors in Access Control Solutions across 16 criteria.
The Access Control Companies Quadrant is a comprehensive industry analysis that provides valuable insights into the global market for Access Control. This quadrant offers a detailed evaluation of key market players, technological advancements, product innovations, and emerging trends shaping the industry. MarketsandMarkets 360 Quadrants evaluated over 40 companies of which the Top 25 Access Control Companies were categorized and recognized as the quadrant leaders.
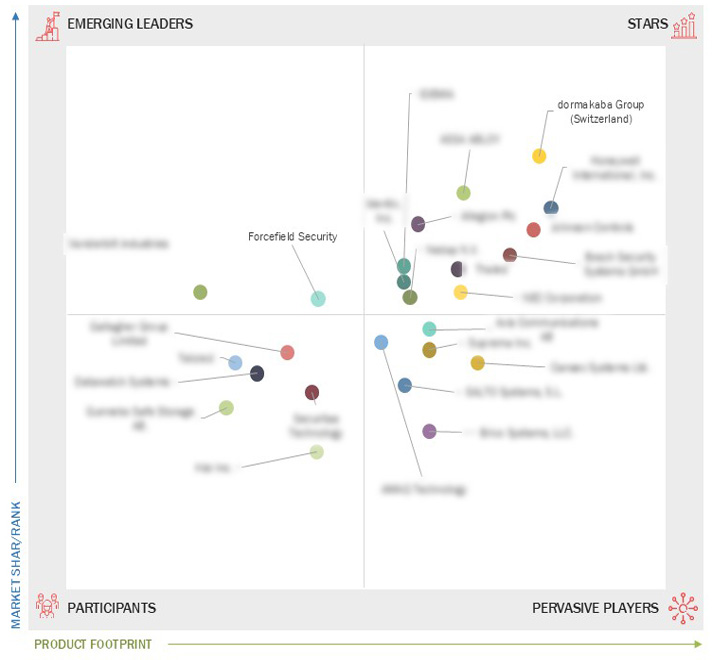
Market Leadership Quadrant
1.1 Study objectives
1.2 Market Definition
1.3 Market Scope
1.3.1 Market Segmentation and Regional Scope
1.3.2 Inclusions and Exclusions
1.3.3 Years Considered
1.3.4 Currency Considered
1.3.5 Units Considered
1.4 Stakeholders
2.1 DRIVERS
2.1.1 Growing awareness about home security
2.1.2 Rising number of smart infrastructure and smart city projects
2.1.3 Ongoing technological advancements and increasing deployment of wireless security systems
2.1.4 Increasing adoption of IoT-based security systems with cloud computing platforms
2.2 RESTRAINTS
2.2.1 High installation, maintenance, and ownership costs of access control systems
2.2.2 Complexity in system integration
2.2.3 Security and privacy concerns related to unauthorized access and data breaches in access control environments
2.3 OPPORTUNITIES
2.3.1 Rapid urbanization in emerging countries
2.3.2 Adoption of ACaaS as cost-effective and flexible solution
2.3.3 Growing implementation of mobile-based access control
2.4 CHALLENGES
2.4.1 Low awareness among users about availability and benefits of advanced security solutions
2.4.2 Availability of free access control services
2.5 INDUSTRY TRENDS
2.6 VALUE CHAIN ANALYSIS
2.7 ECOSYSTEM
2.7.1 SUPPLY SIDE
2.7.2 DEMAND SIDE
2.8 TECHNOLOGY ANALYSIS
2.8.1 KEY TECHNOLOGIES
2.8.1.1 Thermal imaging cameras (thermal camera-based access control)
2.8.1.2 Facial recognition camera technology (face recognition cameras)
2.8.1.3 Video analytics cameras
2.8.1.4 Cloud-based cameras in access control systems
2.8.1.5 Cameras in logical access control
2.8.1.6 Integration of internet of things
2.8.1.7 Contactless biometrics
2.8.3 Adjacent Technologies
2.8.3.1 Comprehensive and proactive security systems
3.1 Key Player Strategies/Right to Win
3.2 Market Share Analysis
3.3 Revenue Analysis
3.4 Company Evaluation Matrix: Key Players, 2023
3.4.1 Definitions and Methodology
3.4.2 Stars
3.4.3 Emerging Leaders
3.4.4 Pervasive Players
3.4.5 Participants
3.4.6 Company Footprint: Key Players, 2023
3.4.6.1 Company Footprint
3.4.6.2 Region Footprint
3.4.6.3 Offering Footprint
3.4.6.4 Area of Application Footprint
3.4.6.5 End User Footprint
3.5 Competitive Scenario and Trend
3.5.1 Product Launches
3.5.2 Deals
4.1 ASSA ABLOY
4.1.1 Business overview
4.1.2 Products offered
4.1.3 Recent developments
4.1.4 MnM view
4.2 DORMAKABA GROUP
4.2.1 Business overview
4.2.2 Products offered
4.2.3 Recent developments
4.2.4 MnM view
4.3 JOHNSON CONTROLS
4.3.1 Business overview
4.3.2 Products offered
4.3.3 Recent developments
4.3.4 MnM view
4.4 ALLEGION PLC
4.4.1 Business overview
4.4.2 Products offered
4.4.3 Recent developments
4.4.4 MnM view
4.5 HONEYWELL INTERNATIONAL INC.
4.5.1 Business overview
4.5.2 Products offered
4.5.3 Recent developments
4.5.4 MnM view
4.6 IDENTIV, INC.
4.6.1 Business overview
4.6.2 Products offered
4.6.3 Recent developments
4.6.4 MnM view
4.7 NEDAP N.V.
4.7.1 Business overview
4.7.2 Products offered
4.7.3 Recent developments
4.7.4 MnM view
4.8 SUPREMA INC.
4.8.1 Business overview
4.8.2 Products offered
4.8.3 MnM view
4.9 BOSCH SECURITY SYSTEMS GMBH
4.9.1 Business overview
4.9.2 Products offered
4.9.3 Recent developments
4.9.4 MnM view
4.10 THALES
4.10.1 Business overview
4.10.2 Products offered
4.10.3 MnM view
4.11 AXIS COMMUNICATIONS
4.11.1 Business overview
4.11.2 Products offered
4.11.3 MnM view
4.12 Gallagher Group Limited
4.12.1 Business overview
4.12.2 Products offered
4.12.3 MnM view
4.13 Telcred
4.13.1 Business overview
4.13.2 Products offered
4.13.3 MnM view
4.14 Datawatch Systems
4.14.1 Business overview
4.14.2 Products offered
4.14.3 MnM view
4.15 Gunnebo Safe Storage AB
4.15.1 Business overview
4.15.2 Products offered
4.15.3 MnM view
4.16 Kisi Inc.
4.16.1 Business overview
4.16.2 Products offered
4.16.3 MnM view
4.17 Securitas Technology
4.17.1 Business overview
4.17.2 Products offered
4.17.3 MnM view
4.18 NEC Corporation
4.18.1 Business overview
4.18.2 Products offered
4.18.3 MnM view
4.19 IDEMIA
4.19.1 Business overview
4.19.2 Products offered
4.19.3 MnM view
4.20 Vanderbilt industries
4.20.1 Business overview
4.20.2 Products offered
4.20.3 MnM view
4.21 Forcefield Security
4.22.1 Business overview
4.22.2 Products offered
4.22.3 MnM view
4.23 Cansec Systems Ltd.
4.23.1 Business overview
4.23.2 Products offered
4.23.3 MnM view
4.24 SALTO Systems, S.L.
4.24.1 Business overview
4.24.2 Products offered
4.24.3 MnM view
4.25 Brivo Systems, LLC.
4.25.1 Business overview
4.25.2 Products offered
4.25.3 MnM view
4.26 AMAG Technology
4.26.1 Business overview
4.26.2 Products offered
4.26.3 MnM view

 igloocompany, Inc.
igloocompany, Inc.
 Jan 2025
Jan 2025

