Comparing 10 vendors in Hardware Security Modules Startups across 0 criteria.
The Hardware Security Modules (HSM) market is undergoing a rapid transformation fueled by the increasing necessity for robust security solutions in an era characterized by digital transactions, electronic payments, and heightened cybersecurity demands. As digital transformation permeates industries, hardware security modules play a critical role by providing a tamper-resistant environment for cryptographic tasks such as key management, which is essential in safeguarding sensitive data against breaches and attacks.
Market Leadership Quadrant
1.1 Study Objectives
1.2 Market Definition
1.3 Study Scope
1.3.1 Markets Covered and Regional Scope
1.3.2 Inclusions and Exclusions
1.3.3 Years Considered
1.4 Currency Considered
1.5 Unit Considered
1.6 Stakeholders
1.7 Limitations
1.8 Summary of Changes
2.1 Introduction
2.2 Market Dynamics
2.2.1 Drivers
2.2.1.1 Increasing data breaches and cyberattacks
2.2.1.2 Need to comply with stringent data security regulations and standards
2.2.1.3 Growing demand for effective management of cryptographic keys
2.2.1.4 Transition to digital transactions and electronic payments
2.2.1.5 Shift toward SDN and NFV in 5G deployments
2.2.2 Restraints
2.2.2.1 High ownership costs associated with hardware security modules
2.2.2.2 Susceptibility to cyberattacks and security breaches
2.2.3 Opportunities
2.2.3.1 Rising volume of data generated by websites and mobile apps
2.2.3.2 Proliferation of connected devices and IoT technologies in smart cities
2.2.3.3 Rise of telemedicine and remote healthcare services
2.2.3.4 Increasing adoption of blockchain and cryptocurrencies
2.2.3.5 Advancements in quantum computing
2.2.4 Challenges
2.2.4.1 Discovering and protecting sensitive data
2.2.4.2 Complexities associated with HSM integration process
2.2.4.3 Rise of complex IT environments
2.3 Trends/Disruptions Impacting Customer Business
2.4 Supply Chain Analysis
2.5 Ecosystem Analysis
2.6 Technology Analysis
2.6.1 Key Technologies
2.6.1.1 AI and ML
2.6.1.2 Contactless smart cards
2.6.1.3 Quantum safe hardware security modules
2.6.2 Complementary Technologies
2.6.2.1 PKI
2.6.3 Adjacent Technologies
2.6.3.1 Blockchain and distributed ledger technologies
2.6.3.2 Digital signatures
2.7 Patent Analysis
2.8 Trade Analysis
2.8.1 Import Data (HS Code 8471)
2.8.2 Export Data (HS Code 8471)
2.9 Key Conferences and Events, 2025–2026
2.10 Porter’s Five Forces Analysis
2.10.1 Threat of New Entrants
2.10.2 Threat of Substitutes
2.10.3 Bargaining Power of Suppliers
2.10.4 Bargaining Power of Buyers
2.10.5 Intensity of Competitive Rivalry
2.11 Impact of AI on Hardware Security Modules Market
3.1 Introduction
3.2 Key Player Strategies/Right to Win, 2020–2024
3.3 Revenue Analysis, 2020–2023
3.4 Market Share Analysis, 2024
3.5 Company Valuation and Financial Metrics, 2024
3.6 Brand/Product Comparison
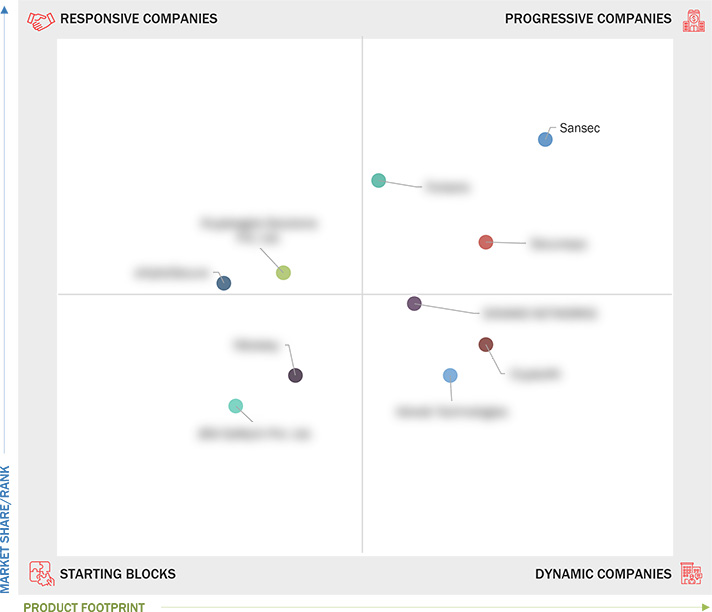
3.7 Company Evaluation Matrix: Startups/SMEs, 2024
3.7.1 Progressive Companies
3.7.2 Responsive Companies
3.7.3 Dynamic Companies
3.7.4 Starting Blocks
3.7.5 Competitive Benchmarking: Startups/SMEs, 2024
3.7.5.1 Detailed list of key startups/SMEs
3.8 Competitive Benchmarking of Key Startups/SMEs
3.9 Competitive Scenario
3.9.1 Product Launches/Developments
3.9.2 Deals
3.9.3 Expansions
3.9.4 Other Developments
4.1 SECUROSYS
4.1.1 Business overview
4.1.2 Products/Solutions/Services offered
4.1.3 Recent developments
4.2 ADWEB TECHNOLOGIES
4.2.1 Business overview
4.2.2 Products/Solutions/Services offered
4.2.3 Recent developments
4.3 ELLIPTICSECURE
4.3.1 Business overview
4.3.2 Products/Solutions/Services offered
4.3.3 Recent developments
4.4 SANSEC
4.4.1 Business overview
4.4.2 Products/Solutions/Services offered
4.4.3 Recent developments
4.5 FORTANIX
4.5.1 Business overview
4.5.2 Products/Solutions/Services offered
4.5.3 Recent developments
4.6 JISA SOFTECH PVT. LTD.
4.6.1 Business overview
4.6.2 Products/Solutions/Services offered
4.6.3 Recent developments
4.7 NITROKEY
4.7.1 Business overview
4.7.2 Products/Solutions/Services offered
4.7.3 Recent developments
4.8 KRYPTOAGILE SOLUTIONS PVT. LTD.
4.8.1 Business overview
4.8.2 Products/Solutions/Services offered
4.8.3 Recent developments
4.9 CRYPTO4A
4.9.1 Business overview
4.9.2 Products/Solutions/Services offered
4.9.3 Recent developments

 Crypto4A Technologies Inc.
Crypto4A Technologies Inc.
 Nov 2025
Nov 2025

