Comparing 11 vendors in Operational Technology (OT) Security Startups across 0 criteria.
The Operational Technology (OT) Security market is experiencing significant growth, driven by the increasing convergence of IT and OT networks and the rising frequency of cyber threats targeting critical infrastructure. As industrial systems become more connected, the risk of attacks that can cause physical damage, production downtime, and safety hazards escalates. OT security solutions are designed to protect industrial control systems (ICS) and SCADA systems from these threats by providing visibility, threat detection, and risk management tailored to the unique requirements of industrial environments.
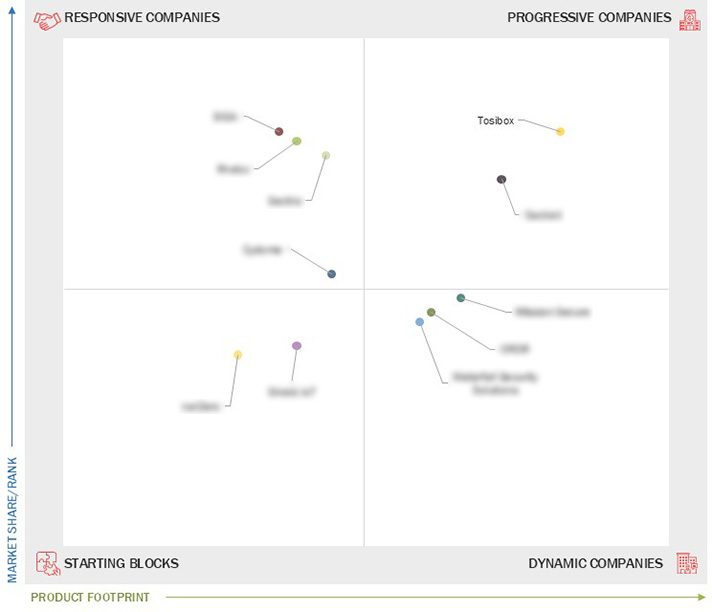
Market Leadership Quadrant
1.1 Study Objectives
1.2 Market Definition
1.3 Study Scope
1.3.1 Markets Covered and Regional Scope
1.3.2 Inclusions and Exclusions
1.3.3 Years Considered
1.4 Currency Considered
1.5 Unit Considered
1.6 Limitations
1.7 Stakeholders
2.1 Introduction
2.2 Market Dynamics
2.2.1 Drivers
2.2.1.1 Convergence of OT and IT networks
2.2.1.2 Need for secure OT networks
2.2.1.3 High procurement costs
2.2.2 Restraints
2.2.2.1 Emerging challenges related to maintenance and upgrades
2.2.2.2 Interoperability and standardization challenges
2.2.2.3 Increasing adoption of AI-powered security solutions
2.2.3 Opportunities
2.2.3.1 Technological advancements in cybersecurity
2.2.3.2 Digital transformation across organizations
2.2.3.3 Rising demand for Industry 4.0 and smart infrastructure
2.2.3.4 Lack of trained security analysts
2.2.4 Challenges
2.2.4.1 Lack of awareness about OT security techniques
2.2.4.2 Complexity pertaining to OT environments
2.3 Trends/Disruptions Impacting Customer Business
2.4 Value Chain Analysis
2.5 Ecosystem Analysis
2.6 Investment and Funding Scenario
2.7 Technology Analysis
2.7.1 Key Technologies
2.7.2 Complementary Technologies
2.7.3 Adjacent Technologies
2.8 Patent Analysis
2.9 Trade Analysis
2.10 Porter’s Five Forces Analysis
2.10.1 Threat of New Entrants
2.10.2 Threat of Substitutes
2.10.3 Bargaining Power of Suppliers
2.10.4 Bargaining Power of Buyers
2.10.5 Intensity of Competitive Rivalry
3.1 Introduction
3.2 Key Player Strategies/Right to Win
3.3 Revenue Analysis
3.4 Market Share Analysis
3.5 Company Valuation and Financial Metrics
3.6 Brand/Product Comparison
3.7 Company Evaluation Matrix: Startups/SMEs
3.7.1 Progressive Companies
3.7.2 Responsive Companies
3.7.3 Dynamic Companies
3.7.4 Starting Blocks
3.7.5 Competitive Benchmarking: Startups/SMEs
3.7.5.1 Detailed list of key startups/SMEs
3.7.5.2 Competitive benchmarking of key startups/SMEs
3.8 Competitive Scenario
3.8.1 Deals
4.1 Tosibox
4.1.1 Business overview
4.1.2 Products/Solutions/Services offered
4.1.3 Recent developments
4.2 Seckiot
4.2.1 Business overview
4.2.2 Products/Solutions/Services offered
4.2.3 Recent developments
4.3 Sectrio
4.3.1 Business overview
4.3.2 Products/Solutions/Services offered
4.3.3 Recent developments
4.4 SIGA
4.4.1 Business overview
4.4.2 Products/Solutions/Services offered
4.4.3 Recent developments
4.5 Rhebo
4.5.1 Business overview
4.5.2 Products/Solutions/Services offered
4.5.3 Recent developments
4.6 Cydome
4.6.1 Business overview
4.6.2 Products/Solutions/Services offered
4.6.3 Recent developments
4.7 Security Solutions
4.7.1 Business overview
4.7.2 Products/Solutions/Services offered
4.7.3 Recent developments
4.8 ORDR
4.8.1 Business overview
4.8.2 Products/Solutions/Services offered
4.8.3 Recent developments
4.9 Mission Secure
4.9.1 Business overview
4.9.2 Products/Solutions/Services offered
4.9.3 Recent developments
4.10 runZero
4.10.1 Business overview
4.10.2 Products/Solutions/Services offered
4.10.3 Recent developments
4.11 Shield-IoT
4.11.1 Business overview
4.11.2 Products/Solutions/Services offered
4.11.3 Recent developments

 marinelink
marinelink
 Feb 2026
Feb 2026

