Comparing 14 vendors in Cybersecurity Startups across 0 criteria.
Cybersecurity plays a vital role in protecting systems, networks, and data from unauthorized access and malicious threats. As digital technology becomes more integrated into daily life, safeguarding information is increasingly critical. The field has evolved alongside computing advancements, with threats growing more sophisticated. Organizations face challenges like ransomware, espionage, and data breaches, prompting the adoption of advanced security solutions. Key areas include network, endpoint, application, and cloud security, along with governance and threat intelligence. Trends such as zero trust models, AI integration, and quantum-safe cryptography are shaping the future of cybersecurity.
Market Leadership Quadrant
1.1 Study Objectives
1.2 Market Definition
1.3 Study Scope
1.3.1 Market Segmentation
1.3.2 Inclusions and Exclusions
1.4 Years Considered
1.5 Currency Considered
1.6 Stakeholders
1.7 Summary of Changes
2.1 Introduction
2.2 Evolution of Cybersecurity
2.2.1 Introduction
2.2.2 Historical Milestones
2.2.2.1 Early Beginning and Concept of Cyber Threats (1971)
2.2.2.2 Rise of Malicious Software and Response (1980–1990)
2.2.2.3 Government Involvement and Regulatory Frameworks (2002)
2.2.2.4 Hacktivism and Political Cyber Threats (2003)
2.2.2.5 Industrial Espionage and Large-scale Cyberattacks
(2009–2010)
2.2.2.6 Era of Ransomware and Advanced Persistent Threats (recent
Years)
2.2.2.7 Regulatory Measures and Data Protection
2.2.2.8 Remote Work and Expansion of Cybersecurity Boundaries
2.2.2.9 Role of AI in Cybersecurity
2.2.3 Future of Cybersecurity
2.2.4 Conclusion
2.3 Cybersecurity Market Framework
2.4 Market Dynamics
2.4.1 Drivers
2.4.1.1 Increased Target-based Cyberattacks Drawing Operational
Disruptions
2.4.1.2 Rise in Need for Protecting Business Assets from Growing
Threats
2.4.1.3 Cybersecurity Mesh Architecture (CSMA) Facilitating
Security Infrastructure
2.4.1.4 Rise in Iot Trends and Need for Automated Cybersecurity
2.4.1.5 Demand for Ensuring Compliance with Government Regulations
and Requirements
2.4.2 Restraints
2.4.2.1 Lack of Skilled Professionals
2.4.2.2 High Implementation and Maintenance Costs
2.4.3 Opportunities
2.4.3.1 Adoption of Cloud-based Cybersecurity Solutions Among Smes
2.4.3.2 Growth in Adoption of Digital Applications Leading to
Increased Cyber Risks
2.4.3.3 Implementation of AI Revolutionizing Incident Response
2.4.4 Challenges
2.4.4.1 Challenges in Deploying and Implementing Cybersecurity
Design Solutions
2.4.4.2 Diverse Nature of Sophisticated Threats
2.4.4.3 Complexity in Vendor Overload and Diversity of Technologies
2.4.4.4 Rising Complexities of Advanced Threats
2.5 Value Chain Analysis
2.5.1 Component/hardware Suppliers
2.5.2 Planning and Designing
2.5.3 Security Solution Providers
2.5.4 Service Providers
2.5.5 System Integrators
2.5.6 Retailers/distributors
2.5.7 End Users
2.6 Ecosystem Analysis
2.7 Porter’s Five Forces Analysis
2.7.1 Threat from New Entrants
2.7.2 Threat from Substitutes
2.7.3 Bargaining Power of Suppliers
2.7.4 Bargaining Power of Buyers
2.7.5 Intensity of Competitive Rivalry
2.8 Technology Analysis
2.8.1 Behavioral Analytics
2.8.2 Blockchain
2.8.3 Cloud Encryption Technologies
2.8.4 Context-aware Security
2.8.5 Defensive AI
2.8.6 Integrated XDR Solutions
2.8.7 Manufacturer Usage Description (MUD)
2.8.8 Zero Trust
2.9 Patent Analysis
2.10 Trends/disruptions Impacting Customer Business
2.11 Key Conferences and Events, 2025–2026
2.12 Investment and Funding Scenario
2.13 Impact of Generative AI on Cybersecurity Market
2.13.1 Top use Cases and Market Potential
2.13.2 Impact of Gen AI on Interconnected and Adjacent Market Ecosystems
2.13.2.1 Cloud Computing
2.13.2.2 Identity and Access Management (IAM)
2.13.2.3 IOT Security
2.13.2.4 Endpoint Protection
2.13.2.5 Security Operations Center (SOC)
2.14 Us Tariff
2.14.1 Introduction
2.14.2 Key Tariff Rates
2.14.3 Price Impact Analysis
2.14.3.1 Strategic Shifts and Emerging Trends
2.14.4 Impact on Country/region
2.14.4.1 Us
2.14.4.2 Europe
2.14.4.3 Asia Pacific
2.14.5 Impact on End-use Industries
3.1 Key Player Strategies/right to Win
3.2 Revenue Analysis, 2020–2024
3.3 Market Share Analysis, 2024
3.4 Brand Comparison
3.5 Company Valuation and Financial Metrics
3.5.1 Company Valuation
3.5.2 Financial Metrics Using EV/EBITDA
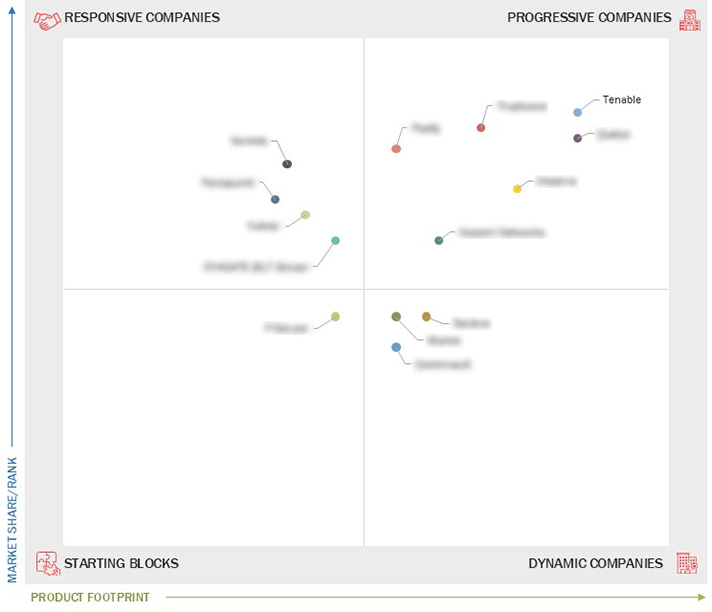
3.6 Company Evaluation Matrix: Startups/SMES, 2024
3.6.1 Progressive Companies
3.6.2 Responsive Companies
3.6.3 Dynamic Companies
3.6.4 Starting Blocks
3.6.5 Competitive Benchmarking: Startups/SMES, 2024
3.6.5.1 Detailed List of Key Startups/SMES
3.6.5.2 Competitive Benchmarking of Key Startups/SMES
3.7 Competitive Scenario
3.7.1 Product Launches & Enhancements
3.7.2 Deals
4.1 COMMVAULT
4.1.1 Business overview
4.1.2 Products/Solutions/Services offered
4.1.3 Recent developments
4.2 CY4GATE
4.2.1 Business overview
4.2.2 Products/Solutions/Services offered
4.2.3 Recent developments
4.3 F-SECURE CORPORATION
4.3.1 Business overview
4.3.2 Products/Solutions/Services offered
4.3.3 Recent developments
4.4 FASTLY
4.4.1 Business overview
4.4.2 Products/Solutions/Services offered
4.4.3 Recent developments
4.5 Forcepoint
4.5.1 Business overview
4.5.2 Products/Solutions/Services offered
4.5.3 Recent developments
4.6 ILLUMIO
4.6.1 Business overview
4.6.2 Products/Solutions/Services offered
4.6.3 Recent developments
4.7 IMPERVA
4.7.1 Business overview
4.7.2 Products/Solutions/Services offered
4.7.3 Recent developments
4.8 NOZOMI NETWORKS
4.8.1 Business overview
4.8.2 Products/Solutions/Services offered
4.8.3 Recent developments
4.9 QUALYS
4.9.1 Business overview
4.9.2 Products/Solutions/Services offered
4.9.3 Recent developments
4.10 SECLORE
4.10.1 Business overview
4.10.2 Products/Solutions/Services offered
4.10.3 Recent developments
4.11 TENABLE INC
4.11.1 Business overview
4.11.2 Products/Solutions/Services offered
4.11.3 Recent developments
4.12 TRUSTWAVE HOLDINGS INC
4.12.1 Business overview
4.12.2 Products/Solutions/Services offered
4.12.3 Recent developments
4.13 VARONIS SYSTEMS
4.13.1 Business overview
4.13.2 Products/Solutions/Services offered
4.13.3 Recent developments
4.14 Yubico
4.14.1 Business overview
4.14.2 Products/Solutions/Services offered
4.14.3 Recent developments

 marketbeat
marketbeat
 Jan 2026
Jan 2026

