Comparing 6 vendors in Digital Forensics Startups across 0 criteria.
The webpage discusses the evolving field of digital forensics, which plays a vital role in investigating cybercrimes and legal proceedings involving digital evidence. It outlines the process of identifying, preserving, analyzing, and presenting digital data from devices like computers and smartphones. The discipline requires a blend of technological expertise and legal knowledge. As digital threats grow, the demand for forensic solutions increases across sectors. The report also highlights market trends, key players, and regional dynamics shaping the future of digital forensics.
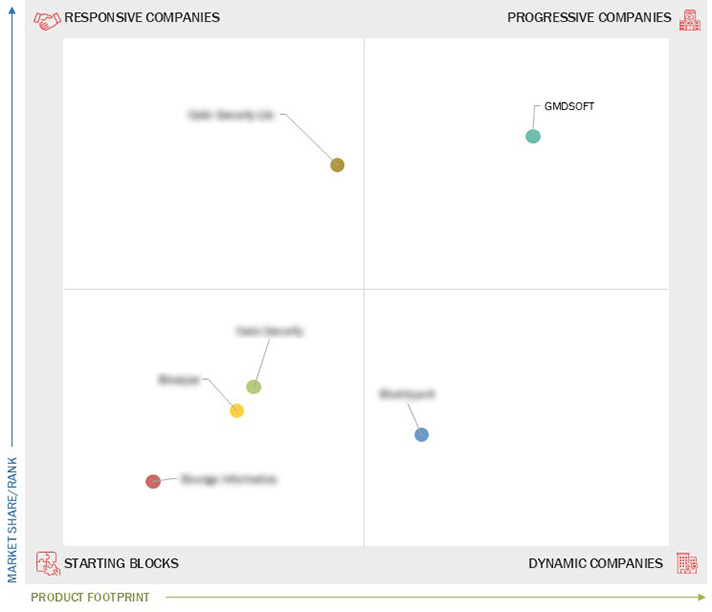
Market Leadership Quadrant
1.1 Study Objectives
1.2 Market Definition
1.3 Study Scope
1.3.1 Markets Covered and Regional Scope
1.3.2 Inclusions and Exclusions
1.3.3 Years Considered
1.4 Currency Considered
1.5 Unit Considered
1.6 Limitations
1.7 Stakeholders
2.1 Introduction
2.2 Market Dynamics
2.2.1 Drivers
2.2.1.1 Rise in cybercrimes to elevate digital forensics as crucial tool for law enforcement
2.2.1.2 Penetration of IoT and BYOD culture
2.2.1.3 Monitoring of remote devices and demand for data security solutions to drive digital forensics
2.2.2 Restraints
2.2.2.1 Lack of skilled professionals
2.2.2.2 High cost of digital forensics tools and services
2.2.3 Opportunities
2.2.3.1 Adoption of digital forensics solutions in highly regulated verticals
2.2.3.2 Increase in cloud computing applications
2.2.3.3 Use of cryptocurrency
2.2.4 Challenges
2.2.4.1 Issues with encryption and lack of digital forensics pre-planning among enterprises
2.3 Trends/Disruptions Impacting Customer Business
2.4 Value Chain Analysis
2.5 Ecosystem Analysis
2.6 Investment and Funding Scenario
2.7 Technology Analysis
2.7.1 Key Technologies
2.7.2 Complementary Technologies
2.7.3 Adjacent Technologies
2.8 Patent Analysis
2.9 Trade Analysis
2.10 Porter’s Five Forces Analysis
2.10.1 Threat of New Entrants
2.10.2 Threat of Substitutes
2.10.3 Bargaining Power of Suppliers
2.10.4 Bargaining Power of Buyers
2.10.5 Intensity of Competitive Rivalry
3.1 Introduction
3.2 Key Player Strategies/Right to Win
3.3 Revenue Analysis
3.4 Market Share Analysis
3.5 Company Valuation and Financial Metrics
3.6 Brand/Product Comparison
3.7 Company Evaluation Matrix: Startups/SMEs
3.7.1 Progressive Companies
3.7.2 Responsive Companies
3.7.3 Dynamic Companies
3.7.4 Starting Blocks
3.7.5 Competitive Benchmarking: Startups/SMEs
3.7.5.1 Detailed list of key startups/SMEs
3.7.5.2 Competitive benchmarking of key startups/SMEs
3.8 Competitive Scenario
3.8.1 Product Launches and Enhancements
3.8.2 Deals
4.1 GMDSOFT
4.1.1 Business overview
4.1.2 Products/Solutions/Services offered
4.1.3 Recent developments
4.2 Optiv Security Ltd.
4.2.1 Business overview
4.2.2 Products/Solutions/Services offered
4.2.3 Recent developments
4.3 BlueVoyant
4.3.1 Business overview
4.3.2 Products/Solutions/Services offered
4.3.3 Recent developments
4.4 Cado Security
4.4.1 Business overview
4.4.2 Products/Solutions/Services offered
4.4.3 Recent developments
4.5 Binalyze
4.5.1 Business overview
4.5.2 Products/Solutions/Services offered
4.5.3 Recent developments
4.6 Bounga Informatica
4.6.1 Business overview
4.6.2 Products/Solutions/Services offered
4.6.3 Recent developments

 Moneylife
Moneylife
 Dec 2023
Dec 2023

