Comparing 9 vendors in Endpoint Security Startups across 0 criteria.
Endpoint security plays a vital role in safeguarding organizational devices such as laptops, smartphones, servers, and IoT systems from evolving cyber threats. With the rise of remote work and cloud computing, traditional antivirus tools have transformed into advanced platforms offering real-time threat detection and response. These solutions integrate technologies like AI-driven threat intelligence, behavioral analysis, and centralized management to ensure data protection and operational continuity. As cyber threats grow more sophisticated, endpoint security becomes a strategic necessity for resilient digital operations.
Market Leadership Quadrant
1.1 Study Objectives
1.2 Market Definition
1.3 Study Scope
1.3.1 Markets Covered and Regional Scope
1.3.2 Inclusions and Exclusions
1.3.3 Years Considered
1.4 Currency Considered
1.5 Unit Considered
1.6 Limitations
1.7 Stakeholders
2.1 Introduction
2.2 Market Dynamics
2.2.1 Drivers
2.2.1.1 Growing surge of cyberattacks
2.2.1.2 Increasing shift toward remote work
2.2.1.3 Rapid growth of IoT devices
2.2.2 Restraints
2.2.2.1 High deployment costs
2.2.2.2 Impact on device performance
2.2.3 Opportunities
2.2.3.1 Growing adoption of cloud
2.2.3.2 Integration of AI/ML into endpoint security solutions
2.2.4 Challenges
2.2.4.1 Shortage of skilled cybersecurity professionals
2.2.4.2 Zero-day vulnerabilities
2.3 Trends/Disruptions Impacting Customer Business
2.4 Value Chain Analysis
2.5 Ecosystem Analysis
2.6 Investment and Funding Scenario
2.7 Technology Analysis
2.7.1 Key Technologies
2.7.2 Complementary Technologies
2.7.3 Adjacent Technologies
2.8 Patent Analysis
2.9 Trade Analysis
2.10 Porter’s Five Forces Analysis
2.10.1 Threat of New Entrants
2.10.2 Threat of Substitutes
2.10.3 Bargaining Power of Suppliers
2.10.4 Bargaining Power of Buyers
2.10.5 Intensity of Competitive Rivalry
3.1 Introduction
3.2 Key Player Strategies/Right to Win
3.3 Revenue Analysis
3.4 Market Share Analysis
3.5 Company Valuation and Financial Metrics
3.6 Brand/Product Comparison
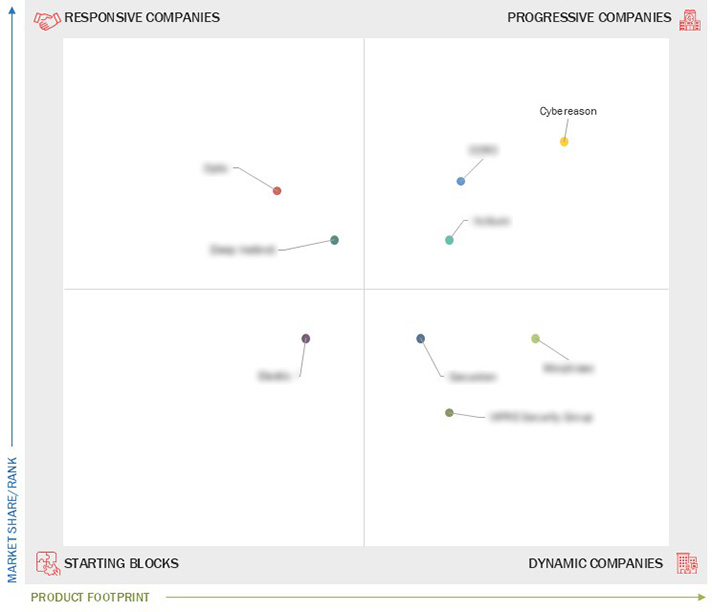
3.7 Company Evaluation Matrix: Startups/SMEs
3.7.1 Progressive Companies
3.7.2 Responsive Companies
3.7.3 Dynamic Companies
3.7.4 Starting Blocks
3.7.5 Competitive Benchmarking: Startups/SMEs
3.7.5.1 Detailed list of key startups/SMEs
3.7.5.2 Competitive benchmarking of key startups/SMEs
3.8 Competitive Scenario
3.8.1 Product Launches
3.8.2 Deals
3.8.3 Expansions
4.1 CYBEREASON
4.1.1 Business overview
4.1.2 Products/Solutions/Services offered
4.1.3 Recent developments
4.2 CORO
4.2.1 Business overview
4.2.2 Products/Solutions/Services offered
4.2.3 Recent developments
4.3 XCITIUM
4.3.1 Business overview
4.3.2 Products/Solutions/Services offered
4.3.3 Recent developments
4.4 DEEP INSTINCT
4.4.1 Business overview
4.4.2 Products/Solutions/Services offered
4.4.3 Recent developments
4.5 OPTIV INC
4.5.1 Business overview
4.5.2 Products/Solutions/Services offered
4.5.3 Recent developments
4.6 MORPHISEC
4.6.1 Business overview
4.6.2 Products/Solutions/Services offered
4.6.3 Recent developments
4.7 Securden
4.7.1 Business overview
4.7.2 Products/Solutions/Services offered
4.7.3 Recent developments
4.8 VIPRE Security Group
4.8.1 Business overview
4.8.2 Products/Solutions/Services offered
4.8.3 Recent developments
4.9 ELASTIC
4.9.1 Business overview
4.9.2 Products/Solutions/Services offered
4.9.3 Recent developments

 TipRanks
TipRanks
 Feb 2026
Feb 2026

