Comparing 15 vendors in Managed Security Services (MSS) Startups across 0 criteria.
Managed Security Services (MSS) have become a critical business priority as organizations confront increasingly complex and high-impact cyber threats. MSS enable organizations to strengthen their security posture by outsourcing continuous monitoring, threat detection, incident response, and compliance management. As cloud computing, remote work, IoT, and digital transformation initiatives expand IT environments, Managed Security Service Providers (MSSPs) deliver round-the-clock protection using advanced analytics, threat intelligence, and security operations expertise. This approach allows organizations to reduce risk, improve resilience, and maintain regulatory compliance without relying solely on internal security resources.
Market Leadership Quadrant
1.1 Study Objectives
1.2 Market Definition
1.3 Study Scope
1.3.1 Market Segmentation and Regional Scope
1.3.2 Inclusions and Exclusions
1.4 Years Considered
1.5 Currency Considered
1.6 Stakeholders
1.7 Summary of Changes
2.1 Introduction
2.2 Market Dynamics
2.2.1 Drivers
2.2.1.1 Increasing need for continuous security monitoring and
incident response
2.2.1.2 Intensifying complexity of cyber threats
2.2.1.3 EVolving regulatory landscape and stringent government
regulations
2.2.1.4 Surge in cloud adoption and prevalence of hybrid
environments
2.2.2 Restraints
2.2.2.1 Lack of visibility and control over outsourced security
functions
2.2.2.2 Limited capabilities for threat-hunting and incident-
response services
2.2.2.3 Reluctance of enterprises to outsource operations
2.2.3 Opportunities
2.2.3.1 Emergence of industry-specific MSS offerings
2.2.3.2 Growing adoption of cloud technology and IoT devices
2.2.3.3 Rising demand for advanced cybersecurity measures
2.2.4 Challenges
2.2.4.1 Balancing scalability with operational efficiency
2.2.4.2 Rising cyberattacks on infrastructure of managed security
service providers
2.2.4.3 Shortage of security professionals
2.2.4.4 Limited capital funding in emerging economies
2.3 Value Chain Analysis
2.3.1 Assessing Security & Architecture Planning
2.3.2 Service Design & Offering
2.3.3 Channel Partners/Mss Distributors
2.3.4 End User Group
2.3.5 Security Monitoring & Threat Detection
2.3.6 Incident Response
2.3.7 MEAsures for Remediation
2.4 Ecosystem Analysis
2.5 Impact of Generative AI on Managed Security Services Market
2.5.1 Generative AI
2.5.2 Top Use Cases and Market Potential in Managed Security Services
Market
2.5.3 Impact of Generative AI on Interconnected and Adjacent Ecosystems
2.5.3.1 SIEM & XDR Platforms
2.5.3.2 Soar Systems
2.5.3.3 Cloud Security
2.5.3.4 Artificial Intelligence (AI)/Machine Learning (ML) Analytics
2.5.3.5 IoT & Managed Security Services
2.6 Porter’s Five Forces Analysis
2.6.1 Threat of New Entrants
2.6.2 Threat of Substitutes
2.6.3 Bargaining Power of Suppliers
2.6.4 Bargaining Power of Buyers
2.6.5 Intensity of Competitive Rivalry
2.7 Technology Analysis
2.7.1 Key Technologies
2.7.1.1 AI/ML and managed security services
2.7.1.2 Cloud-based security solutions
2.7.1.3 Security information and event management
2.7.1.4 Security orchestration, automation, and response
2.7.2 Complementary Technologies
2.7.2.1 Threat intelligence platforms
2.7.2.2 Identity threat detection and response
2.7.3 Adjacent Technologies
2.7.3.1 Zero-trust architecture
2.7.3.2 IoT and managed security services
2.7.3.3 Extended and detection response
2.8 Patent Analysis
2.9 Impact of US Tariff – Managed Security Services Market
2.9.1 Introduction
2.9.2 Key Tariff Rates
2.9.3 Price Impact Analysis
2.9.4 Impact on Country/Region
2.9.4.1 North America
2.9.4.2 Europe
2.9.4.3 Asia Pacific
2.9.5 Impact on End-Use Industries
2.10 Trends/Disruptions Impacting Customer Business
2.11 Managed Security Services Market: Business Models
2.12 Key Conferences & Events in 2025
2.13 Investment and Funding Scenario
3.1 Key Player Strategies/Right to Win
3.2 Revenue Analysis, 2020–2024
3.3 Market Share Analysis, 2024
3.4 Brand/Product Comparison
3.5 Company Valuation and Financial Metrics
3.5.1 Company Valuation
3.5.2 Financial Metrics of Key Vendors
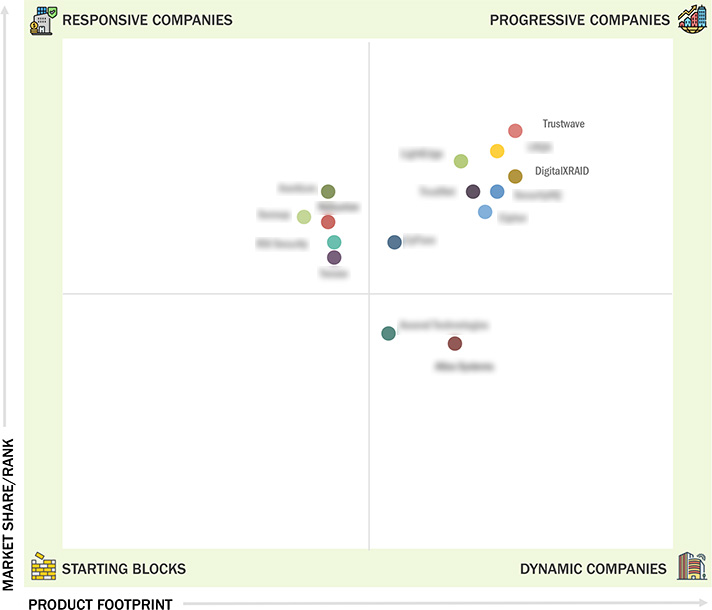
3.6 Company Evaluation Matrix: Startups/SMEs, 2024
3.6.1 Progressive Companies
3.6.2 Responsive Companies
3.6.3 Dynamic Companies
3.6.4 Starting Blocks
3.6.5 Competitive Benchmarking: Startups/SMEs, 2024
3.6.5.1 Detailed list of key startups/SMEs
3.6.5.2 Competitive benchmarking of key startups/SMEs
3.7 Competitive Scenario
3.7.1 Product Launches & Developments
3.7.2 Deals
4.1 TRUSTWAVE
4.1.1 Business overview
4.1.2 Products/Solutions/Services offered
4.1.3 Recent developments
4.2 LRQA NETTITUDE
4.2.1 Business overview
4.2.2 Products/Solutions/Services offered
4.2.3 Recent developments
4.3 LIGHTEDGE
4.3.1 Business overview
4.3.2 Products/Solutions/Services offered
4.3.3 Recent developments
4.4 DIGITALXRAID
4.4.1 Business overview
4.4.2 Products/Solutions/Services offered
4.4.3 Recent developments
4.5 SECURITY HQ
4.5.1 Business overview
4.5.2 Products/Solutions/Services offered
4.5.3 Recent developments
4.6 TRUSTNET
4.6.1 Business overview
4.6.2 Products/Solutions/Services offered
4.6.3 Recent developments
4.7 CIPHER
4.7.1 Business overview
4.7.2 Products/Solutions/Services offered
4.7.3 Recent developments
4.8 CYFLARE
4.8.1 Business overview
4.8.2 Products/Solutions/Services offered
4.8.3 Recent developments
4.9 AVERTIUM
4.9.1 Business overview
4.9.2 Products/Solutions/Services offered
4.9.3 Recent developments
4.10 RSI SECURITY
4.10.1 Business overview
4.10.2 Products/Solutions/Services offered
4.10.3 Recent developments
4.11 TECEZE
4.11.1 Business overview
4.11.2 Products/Solutions/Services offered
4.11.3 Recent developments
4.12 NETSURION
4.12.1 Business overview
4.12.2 Products/Solutions/Services offered
4.12.3 Recent developments
4.13 SECNAP
4.13.1 Business overview
4.13.2 Products/Solutions/Services offered
4.13.3 Recent developments
4.14 ASCEND TECHNOLOGIES
4.14.1 Business overview
4.14.2 Products/Solutions/Services offered
4.14.3 Recent developments
4.15 ATLAS SYSTEMS
4.15.1 Business overview
4.15.2 Products/Solutions/Services offered
4.15.3 Recent developments

 einpresswire
einpresswire
 Oct 2025
Oct 2025

