Comparing 26 vendors in Middle East Cybersecurity Startups across 0 criteria.
Cybersecurity in the Middle East is becoming increasingly vital due to rising digital adoption and the region’s strategic importance in sectors like oil and gas. Organizations face growing threats from advanced persistent groups, ransomware, and hacktivists targeting critical infrastructure. Governments and enterprises are responding with robust cybersecurity strategies, driven by regulatory compliance, cloud adoption, and smart city initiatives. Despite challenges like budget constraints and talent shortages, the market is expanding rapidly, supported by innovation and increased investment in digital security solutions.
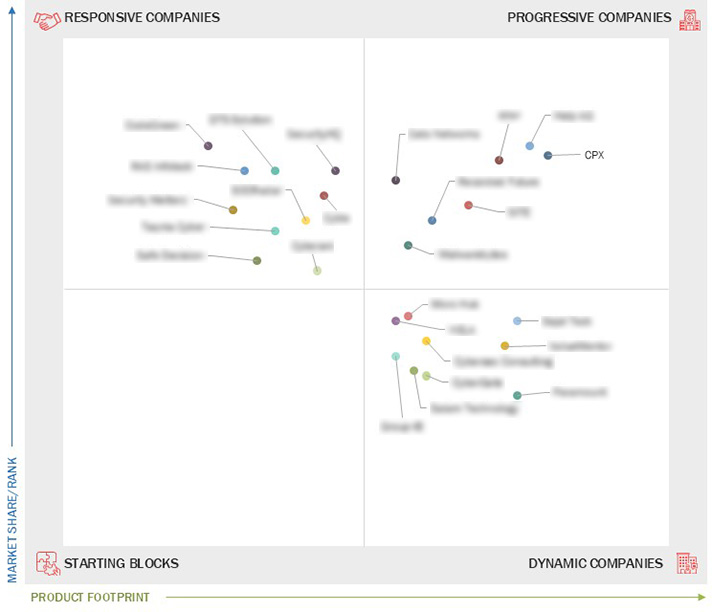
Market Leadership Quadrant
1.1 Study Objectives
1.2 Market Definition
1.3 Study Scope
1.3.1 Markets Covered and Regional Scope
1.3.2 Inclusions and Exclusions
1.3.3 Years Considered
1.4 Currency Considered
1.5 Unit Considered
1.6 Limitations
1.7 Stakeholders
2.1 Introduction
2.2 Market Dynamics
2.2.1 Drivers
2.2.1.1 Accelerated digital transformation across sectors
2.2.1.2 Geopolitical tensions and rise of state-sponsored cyber threats
2.2.1.3 Regulatory initiatives for evolving threat environment
2.2.1.4 AI-powered attacks compelling evolution of cyber defense strategies
2.2.2 Restraints
2.2.2.1 Budgetary constraints on allocation of resources
2.2.2.2 Resistance to emerging security technologies
2.2.3 Opportunities
2.2.3.1 Investments by governments and businesses to enhance cybersecurity infrastructure
2.2.3.2 Spike in demand for cyber-insurance policies
2.2.3.3 Robust development of cybersecurity services
2.2.3.4 Burgeoning startup ecosystem
2.2.4 Challenges
2.2.4.1 Third-party dependencies exposing weaknesses in cybersecurity landscape
2.2.4.2 Shortage of skilled workforce
2.3 Trends/Disruptions Impacting Customer Business
2.4 Value Chain Analysis
2.5 Ecosystem Analysis
2.6 Investment and Funding Scenario
2.7 Technology Analysis
2.7.1 Key Technologies
2.7.2 Complementary Technologies
2.7.3 Adjacent Technologies
2.8 Patent Analysis
2.9 Trade Analysis
2.10 Porter’s Five Forces Analysis
2.10.1 Threat of New Entrants
2.10.2 Threat of Substitutes
2.10.3 Bargaining Power of Suppliers
2.10.4 Bargaining Power of Buyers
2.10.5 Intensity of Competitive Rivalry
3.1 Introduction
3.2 Key Player Strategies/Right to Win
3.3 Revenue Analysis
3.4 Market Share Analysis
3.5 Company Valuation and Financial Metrics
3.6 Brand/Product Comparison
3.7 Company Evaluation Matrix: Startups/SMEs
3.7.1 Progressive Companies
3.7.2 Responsive Companies
3.7.3 Dynamic Companies
3.7.4 Starting Blocks
3.7.5 Competitive Benchmarking: Startups/SMEs
3.7.5.1 Detailed list of key startups/SMEs
3.7.5.2 Competitive benchmarking of key startups/SMEs
3.8 Competitive Scenario
3.8.1 Product Launches and Enhancements
3.8.2 Deals
4.1 Help AG
4.1.1 Business overview
4.1.2 Products/Solutions/Services offered
4.1.3 Recent developments
4.2 sirar
4.2.1 Business overview
4.2.2 Products/Solutions/Services offered
4.2.3 Recent developments
4.3 CPX
4.3.1 Business overview
4.3.2 Products/Solutions/Services offered
4.3.3 Recent developments
4.4 Cato Networks
4.4.1 Business overview
4.4.2 Products/Solutions/Services offered
4.4.3 Recent developments
4.5 RECORDED FUTURE
4.5.1 Business overview
4.5.2 Products/Solutions/Services offered
4.5.3 Recent developments
4.6 SITE
4.6.1 Business overview
4.6.2 Products/Solutions/Services offered
4.6.3 Recent developments
4.7 MALWAREBYTES
4.7.1 Business overview
4.7.2 Products/Solutions/Services offered
4.7.3 Recent developments
4.8 Cyble
4.8.1 Business overview
4.8.2 Products/Solutions/Services offered
4.8.3 Recent developments
4.9 Cyberani
4.9.1 Business overview
4.9.2 Products/Solutions/Services offered
4.9.3 Recent developments
4.10 SecurityHQ
4.10.1 Business overview
4.10.2 Products/Solutions/Services offered
4.10.3 Recent developments
4.11 DTS Solutions
4.11.1 Business overview
4.11.2 Products/Solutions/Services offered
4.11.3 Recent developments
4.12 SOCRadar
4.12.1 Business overview
4.12.2 Products/Solutions/Services offered
4.12.3 Recent developments
4.13 Safe Decision
4.13.1 Business overview
4.13.2 Products/Solutions/Services offered
4.13.3 Recent developments
4.14 Taqnia Cyber
4.14.1 Business overview
4.14.2 Products/Solutions/Services offered
4.14.3 Recent developments
4.15 Security Matterz
4.15.1 Business overview
4.15.2 Products/Solutions/Services offered
4.15.3 Recent developments
4.16 RAS Infotech
4.16.1 Business overview
4.16.2 Products/Solutions/Services offered
4.16.3 Recent developments
4.17 CodeGreen
4.17.1 Business overview
4.17.2 Products/Solutions/Services offered
4.17.3 Recent developments
4.18 Moro Hub
4.18.1 Business overview
4.18.2 Products/Solutions/Services offered
4.18.3 Recent developments
4.19 KELA
4.19.1 Business overview
4.19.2 Products/Solutions/Services offered
4.19.3 Recent developments
4.20 Sejel Tech
4.20.1 Business overview
4.20.2 Products/Solutions/Services offered
4.20.3 Recent developments
4.21 ValueMentor
4.21.1 Business overview
4.21.2 Products/Solutions/Services offered
4.21.3 Recent developments
4.22 Cybersec Consulting
4.22.1 Business overview
4.22.2 Products/Solutions/Services offered
4.22.3 Recent developments
4.23 CYBERGATE
4.23.1 Business overview
4.23.2 Products/Solutions/Services offered
4.23.3 Recent developments
4.24 Paramount
4.24.1 Business overview
4.24.2 Products/Solutions/Services offered
4.24.3 Recent developments
4.25 Salam Technology
4.25.1 Business overview
4.25.2 Products/Solutions/Services offered
4.25.3 Recent developments
4.26 GROUP-IB
4.26.1 Business overview
4.26.2 Products/Solutions/Services offered
4.26.3 Recent developments

 portapiment.com
portapiment.com
 Jan 2026
Jan 2026

