Comparing 6 vendors in Security Service Edge (SSE) Startups across 0 criteria.
The Security Service Edge (SSE) market is rapidly evolving as organizations prioritize stronger cybersecurity amid growing digital ecosystems. Key drivers include the integration of Cloud Access Security Broker (CASB) capabilities and the adoption of zero trust frameworks. As businesses shift to cloud operations and IoT, cyber threats are rising, pushing demand for comprehensive security solutions. The rise of remote and hybrid work models further underscores the need for secure, scalable network infrastructures, fueling the growth of advanced SSE technologies.
Market Leadership Quadrant
1.1 Study Objectives
1.2 Market Definition
1.2.1 Inclusions & Exclusions
1.3 Market Scope
1.3.1 Market Segmentation
1.3.2 Years Considered
1.4 Currency Considered
1.5 Stakeholders
1.6 Summary of Changes
2.1 Introduction
2.1.1 Drivers
2.1.1.1 Widespread adoption of remote and hybrid work models
2.1.1.2 Rising need for unified network security architecture
2.1.1.3 Integration of CASB into organization security framework
2.1.1.4 Rising demand for zero-trust security
2.1.1.5 Compliance with stringent regulations and data protection laws
2.1.2 Restraints
2.1.2.1 Complexities in integrating with existing infrastructure
2.1.2.2 Shortage of skilled professionals
2.1.3 Opportunities
2.1.3.1 Integration of AI and ML technologies with SSE solutions
2.1.3.2 Combination of multiple security and network access technologies
2.1.4 Challenges
2.1.4.1 Managing and securing high volumes of network traffic
2.1.4.2 Reforming security policies
2.2 Value Chain Analysis
2.3 Ecosystem Analysis
2.4 Porter’s Five Forces Analysis
2.4.1 Threat of New Entrants
2.4.2 Threat of Substitutes
2.4.3 Bargaining Power of Suppliers
2.4.4 Bargaining Power of Buyers
2.4.5 Intensity of Competitive Rivalry
2.5 Trends/Disruptions Impacting Customer Business
2.6 Technology Analysis
2.6.1 Key Technologies
2.6.1.1 Zero Trust Network Access (ZTNA)
2.6.1.2 Secure Web Gateway (SWG)
2.6.1.3 Data Loss Prevention (DLP)
2.6.1.4 Remote Browser Isolation (RBI)
2.6.1.5 Sandboxing
2.6.2 Complementary Technologies
2.6.2.1 Software-defined Perimeter (SDP)
2.6.2.2 AI/ML
2.6.2.3 Security Orchestration, Automation, and Response (SOAR)
2.6.3 Adjacent Technologies
2.6.3.1 Edge computing & IoT security
2.6.3.2 Cloud computing
2.7 Patent Analysis
2.7.1 List of Top Patents in Security Service Edge (SSE) Market, 2022–2025
2.8 Investment and Funding Scenario
2.9 Impact of Generative AI on Security Service Edge (SSE) Market
2.9.1 Top Use Cases and Market Potential
2.9.2 Impact of Gen AI on Interconnected and Adjacent Ecosystems
2.9.2.1 Secure Access Service Edge (SASE)
2.9.2.2 Identity and Access Management (IAM)
2.9.2.3 Security-as-a-Service
2.9.2.4 Cloud computing
2.9.2.5 Endpoint security
2.10 Key Conferences and Events, 2025
3.1 Overview
3.2 Key Player Strategies/Right to Win, 2022–2025
3.3 Revenue Analysis, 2019–2023
3.4 Market Share Analysis, 2023
3.5 Brand Comparison
3.6 Company Valuation and Financial Metrics
3.6.1 Company Valuation
3.6.2 Financial Metrics Using EV/EBITDA
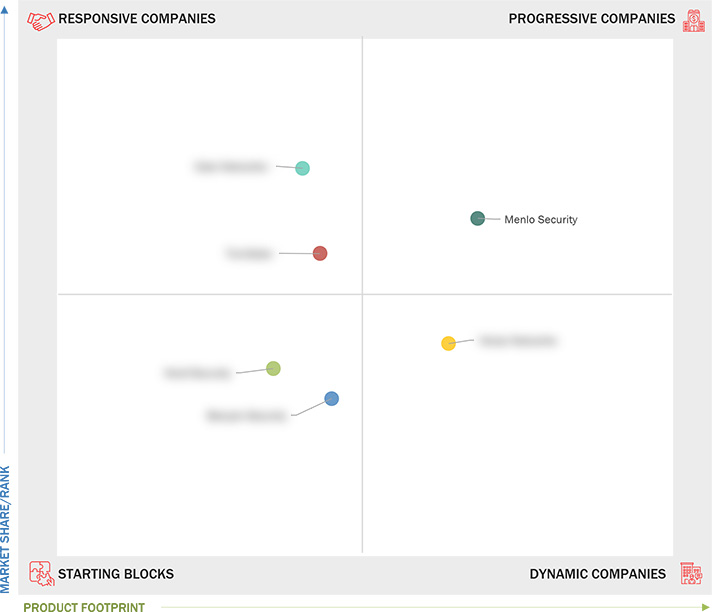
3.7 Company Evaluation Matrix: Startups/SMEs, 2023
3.7.1 Progressive Companies
3.7.2 Responsive Companies
3.7.3 Dynamic Companies
3.7.4 Starting Blocks
3.7.5 Competitive Benchmarking: Startups/SMEs, 2023
3.7.5.1 Detailed list of key startups/SMEs
3.7.5.2 Competitive benchmarking of key startups/SMEs
3.8 Competitive Scenario
3.8.1 Product Launches and Enhancements
3.8.2 Deals
4.1 CATO NETWORKS
4.1.1 Business overview
4.1.2 Products/Solutions/Services offered
4.1.3 Recent developments
4.2 MENLO SECURITY
4.2.1 Business overview
4.2.2 Products/Solutions/Services offered
4.2.3 Recent developments
4.3 VERSA NETWORKS
4.3.1 Business overview
4.3.2 Products/Solutions/Services offered
4.3.3 Recent developments
4.4 NORD SECURITY
4.4.1 Business overview
4.4.2 Products/Solutions/Services offered
4.4.3 Recent developments
4.5 TWINGATE
4.5.1 Business overview
4.5.2 Products/Solutions/Services offered
4.5.3 Recent developments
4.6 BANYAN SECURITY
4.6.1 Business overview
4.6.2 Products/Solutions/Services offered
4.6.3 Recent developments

 Cato Networks
Cato Networks
 Jan 2026
Jan 2026

