Comparing 4 vendors in Supply Chain Security Startups across 0 criteria.
Supply Chain Security oversees the entire production flow from raw materials to final delivery. Supply chain security focuses on mitigating risks in logistics, transportation, and other areas by embedding cybersecurity principles. It addresses threats like data breaches and ransomware, which can disrupt operations and harm reputation. Technologies like AI and blockchain enhance security by detecting anomalies and ensuring data integrity. Key concerns include data protection, visibility, fraud prevention, and third-party risks. The supply chain security market is poised for significant growth, driven by increasing cyber threats and the need for robust security solutions.
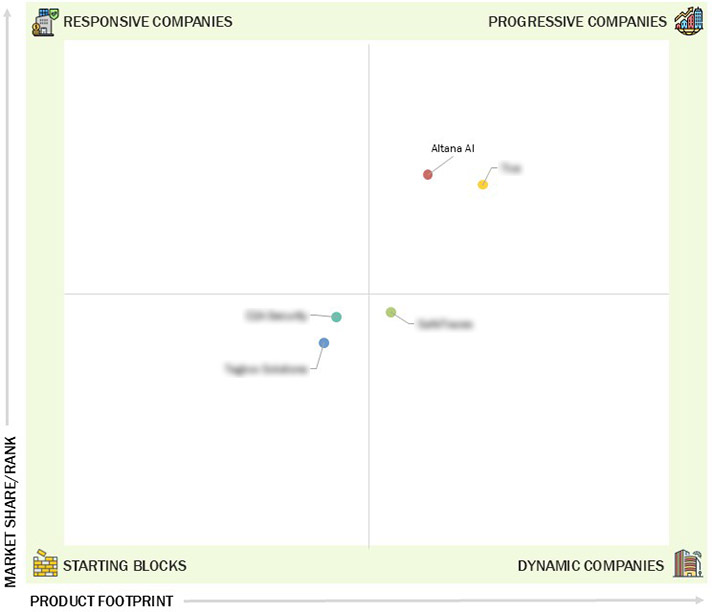
Market Leadership Quadrant
1.1 Study Objectives
1.2 Market Definition
1.3 Study Scope
1.3.1 Markets Covered and Regional Scope
1.3.2 Inclusions and Exclusions
1.3.3 Years Considered
1.4 Currency Considered
1.5 Unit Considered
1.6 Limitations
1.7 Stakeholders
2.1 Introduction
2.2 Market Dynamics
2.2.1 Drivers
2.2.1.1 Rising incidences of cyberattacks across supply chains
2.2.1.2 Growing need for supply chain transparency
2.2.1.3 Upsurge and innovation in advanced technologies
2.2.1.4 Regulatory compliance and stringent government mandates
2.2.2 Restraints
2.2.2.1 Budgetary constraints among small and emerging start-ups in developing economies
2.2.2.2 Shortage of skilled professionals
2.2.3 Opportunities
2.2.3.1 Rapid growth in eCommerce sector
2.2.3.2 Advancing risk prediction and management in supply chains
2.2.3.3 Increasing IoT devices in supply chain
2.2.4 Challenges
2.2.4.1 Limited awareness about supply chain security among organizations
2.2.4.2 Third-party risks and insider threats
2.3 Trends/Disruptions Impacting Customer Business
2.4 Value Chain Analysis
2.5 Ecosystem Analysis
2.6 Investment and Funding Scenario
2.7 Technology Analysis
2.7.1 Key Technologies
2.7.2 Complementary Technologies
2.7.3 Adjacent Technologies
2.8 Patent Analysis
2.9 Trade Analysis
2.10 Porter’s Five Forces Analysis
2.10.1 Threat of New Entrants
2.10.2 Threat of Substitutes
2.10.3 Bargaining Power of Suppliers
2.10.4 Bargaining Power of Buyers
2.10.5 Intensity of Competitive Rivalry
3.1 Introduction
3.2 Key Player Strategies/Right to Win
3.3 Revenue Analysis
3.4 Market Share Analysis
3.5 Company Valuation and Financial Metrics
3.6 Brand/Product Comparison
3.7 Company Evaluation Matrix: Startups/SMEs
3.7.1 Progressive Companies
3.7.2 Responsive Companies
3.7.3 Dynamic Companies
3.7.4 Starting Blocks
3.7.5 Competitive Benchmarking: Startups/SMEs
3.7.5.1 Detailed list of key startups/SMEs
3.7.5.2 Competitive benchmarking of key startups/SMEs
3.8 Competitive Scenario
3.8.1 Product Launches and Enhancements
3.8.2 Deals
4.1 Tive
4.1.1 Business overview
4.1.2 Products/Solutions/Services offered
4.1.3 Recent developments
4.2 Altana AI
4.2.1 Business overview
4.2.2 Products/Solutions/Services offered
4.2.3 Recent developments
4.3 Safetraces
4.3.1 Business overview
4.3.2 Products/Solutions/Services offered
4.3.3 Recent developments
4.4 C2A Security
4.4.1 Business overview
4.4.2 Products/Solutions/Services offered
4.4.3 Recent developments
4.5 TagBox Solutions
4.5.1 Business overview
4.5.2 Products/Solutions/Services offered
4.5.3 Recent developments

 einpresswire
einpresswire
 Jan 2026
Jan 2026

