Best Industrial Control Systems Security Solutions
Industrial Control Systems Security (ICS security) is defined as the ability of organizations to secure their automation processes and related critical information from cyber intrusions for uninterrupted and sustained productivity of utilities, grids, transportation systems, and manufacturing plants. Industrial Control Systems security solutions cover various types of control systems used in industries for operations. Supervisory Control and Data Acquisition (SCADA), Distributed Control System (DCS), and Programmable Logic Controllers (PLC) are used to remotely manage critical industrial infrastructures from a central control room. Securing these systems has become a major concern in the present age of advanced persistent threats, such as Stuxnet and Havex RAT. The highly sophisticated and severe nature of these threats is prompting various security solution providers to customize their offerings according to industry demand.
Industrial Control Systems security solutions and software consist of a compressive array of technologies such as Distributed Denial of Service (DDoS), Intrusion Detection System/Intrusion Prevention System (IDS/IPS), antivirus/anti-malware, firewall, virtualization security, Security Information and Event Management (SIEM), SCADA encryption, Unified Threat Management (UTM), Data Loss Prevention (DLP), Identity and Access Management (IAM), and others. Professional services for ICS security include offerings from primary operational support to entire lifecycle management services.
360Quadrants recognizes the below-listed companies as the Best Industrial Control Systems Security Solutions -
Top 10 Industrial Control Systems Security Solutions in 2020:
- CISCO SYSTEMS
- SIEMENS AG
- IBM CORPORATION
- HONEYWELL
- ABB
- TREND MICRO INCORPORATED
- SYMANTEC CORPORATION
- FORTINET
- GE
- MCAFEE
Top Features of Industrial Control Systems Security Solutions
Industrial control System security refers to the information securing process by preventing, detecting and reacting to various types of attacks such as malicious software, ransomware attacks, DDOS attacks and intrusion attacks on the system. Some of the key features are:
- Anomaly Detection
- Authentication
- Content Filtering
- Endpoint Intelligence
- Incident Forensics
- Intelligence Reports
- Intrusion Prevention
- Proactive Alerts
- Security Auditing
- Workload Protection
Top solutions offered
Industrial Control Systems Security (ICS Security) is interpreted as the capability of institutions to safeguard their automation processes and related important data from cyberattacks for continued and uninterrupted efficiency of utilities, grids, transport networks, and production lines. Some of the solutions provided are:
- Antimalware/ Antivirus
- Distributed Denial of Service Mitigation
- Encryption
- Firewall
- Identity and Access Management
- Intrusion Detection System/ Intrusion Prevention System
- Security and Vulnerability Management
- Security Configuration Management
- Security Information and Event Management
- Whitelisting
Top Growing Companies
- Carbon Black
- Bayshore Networks
- Indegy
- Nozomi Networks
- CyberArk
- Claroty
- SecurityMatters
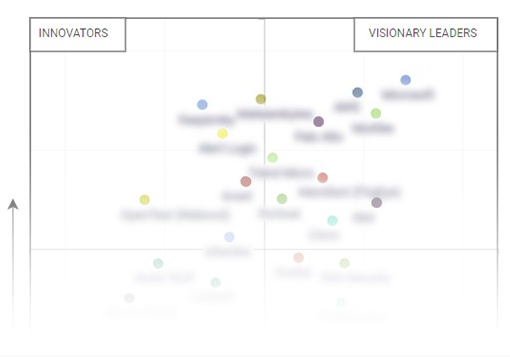
100+ companies offering Industrial Control Systems Security Solutions were analyzed of which 50 companies were shortlisted and categorized on a quadrant under Visionary Leaders, Innovators, Dynamic Differentiators, and Emerging Companies.
ABB, Belden, Check Point Software Technologies, Cisco Systems, Fortinet, GE, Honeywell, McAfee, and Siemens have been identified as visionary leaders as they have established product portfolios and a robust market presence and business strategy.
Kaspersky Lab, Bayshore Networks, Indegy, Nozomi Networks, Schneider Electric, and Symantec have been identified as innovators as these vendors have a very focused product portfolio. However, they do not have very strong growth strategies for their overall business.
BAE Systems, Carbon Black, CyberArk, Claroty, and SecurityMatters have been identified as emerging companies. They do not have very strong business strategies as compared to other established vendors. They might be new entrants and require some more time before gaining significant traction in the market. FireEye, IBM, Raytheon, Rockwell Automation, and Trend Micro have been recognized as dynamic differentiators.
The competitive leadership mapping (Quadrant) showcased below provides information for 50 major players offering Industrial Control Systems security solutions and software. Vendor evaluations are based on two broad categories: product offering and business strategy. Each category carries various criteria, based on which vendors have been evaluated. The evaluation criteria considered under product offering includes the Products features and functionality, Deployment, Services and Pricing. The evaluation criteria considered under business strategy includes the reach (geographic presence), industry coverage, financial strength and partner ecosystem. Products offered by these players are loaded with several features and capabilities.
Visionary Leaders generally receive high scores for most evaluation criteria. They have a strong product portfolio, a very strong market presence, and strong business strategies. They provide mature and reputable Industrial Control Systems security solutions and software. They also have strong business strategies. ABB, Belden, Check Point Software Technologies, Cisco Systems, Fortinet, GE, Honeywell, McAfee, and Siemens have been listed as visionary leaders.
Dynamic Differentiators are established vendors with very strong business strategies. However, they have a weak product portfolio. They generally focus on a specific type of technology related to the product. FireEye, IBM, Raytheon, Rockwell Automation, and Trend Micro have been considered as dynamic differentiators.
Innovators demonstrate substantial product innovation as compared to their competitors. They have a very focused product portfolio. However, they do not have strong growth strategies for their overall business. Kaspersky Lab, Bayshore Networks, Indegy, Nozomi Networks, Schneider Electric, and Symantec have been categorized as innovators.
Emerging Companies have niche product offerings and are starting to gain their position in the market. They do not have strong business strategies as compared to other established vendors. They might be new entrants in the market and require some time to achieve significant traction in the market. BAE Systems, Carbon Black, CyberArk, Claroty, and SecurityMatters have been categorized as emerging companies.
Industrial Control Systems Security Solutions- VENDOR EVALUATIONS & SCORING AREAS
STRENGTH OF PRODUCT PORTFOLIO
- Product Features & Functionality
- This criterion evaluates each vendor’s current product capabilities, quality, and features/functionality. Vendors who offer a relevant suite of products across a diverse set of vertical markets are scored higher. Vendors offering distinguished features in multiple application areas, along with a wider solution set and partner ecosystem are also rated higher.
- Deployment
- This criterion evaluates each vendor’s offering which includes current services/products/solutions and its variants offered, type of pre-integrated systems (i.e. hardware, software specifications, and associated services), customized specifications, additional services related to the market, service subscription packages, and pricing details.
- Services
- A vendor's product quality is assessed based on industry standards along with the assessment of their pre- and post-sales service. It includes various ways using which each vendor offers technical support to customers. Frequency and various levels of customer support that complement market offerings are also taken into account while rating vendors. Along with this, Six Sigma and similar practices to improve the product quality also help improve a vendor’s rating.
- Pricing
- A vendor’s pricing options are evaluated under this criterion to understand the competitiveness and flexibility of the vendor to cater to various client requirements.
>BUSINESS STRATEGY EXCELLENCE
- Geographic Footprint
- This is an assessment of the organization or business unit’s direct and indirect presence across five major regions: North America, Europe, Asia Pacific (APAC), the Middle East and Africa (MEA), and Latin America. It includes each vendor’s ability to deliver and deploy its offerings at client locations and provide customer support worldwide.
- Sector Footprint
- This is an assessment of the organization or business unit’s offerings across various sectors. It includes each vendor’s ability to deliver and deploy its offerings to the different verticals present in the market.
- Partner Ecosystem
- A vendor's strategy for delivering and deploying its offerings, including channels and partners to target a worldwide installed client base are evaluated under this criterion. A vendor’s strategies to manage worldwide channels and address un-catered and new target audience around the globe is also one of the factors that determines his score.
- Financial Strength
- This is an assessment of the organization or business unit’s overall financial health, and the size of its customer base. A vendor's revenue for the current financial year, specifically the revenue generated by the firm through their market offerings; estimated Y-o-Y revenue growth; revenue breakdown by region and industry verticals; and approximate number of customers installed are all evaluated prior to scoring. Along with this, a vendor’s developments over the past year, such as new product(s) launched, new customers acquired, patents registered, and R&D spending specific to the market, are also taken into consideration. A vendor’s future plans related to the targeted market are also considered for scoring.
The major functionalities have been studied are as below:
ANTIMALWARE/ANTIVIRUS
Antimalware/antivirus software is a critical component or layer of protection for securing ICS from external intrusions. Antimalware or antivirus software is used to prevent, detect, and remove viruses, and other malicious malware, such as rootkits, spyware, adware, Trojans, and worms. A virus is a program or a piece of code that is loaded into the systems to infect computer programs and data files; it can cause unexpected shut down of systems. Most of the industries across the globe are suffering from virus and malware attacks. Hence, it is important for businesses to install and update their antivirus programs to defend themselves from the virus attacks. Stuxnet, Duqu, Shamoon/Disttrack, BlackEnergy, and Night Dragon are some of the viruses that usually target ICS networks. For instance, in December 2016, the Ukrainian electric power industry was attacked, in which, hackers targeted the electric power industry with the BlackEnergy Trojan. Therefore, there is a high need for antivirus software to secure industrial processes. Vendors such as Symantec, Kaspersky Lab, Trend Micro, and Fortinet actively install antivirus software into the control systems.
DISTRIBUTED DENIAL OF SERVICE MITIGATION
In recent years, DDoS attacks have become very frequent. DDoS attacks are usually generated from multiple connected devices that are scattered over the internet. DDoS focuses mainly on the network infrastructure and tries to saturate the network with huge volumes of traffic. Earlier, the primary targets of DDoS were financial institutions, but after many surveys on industrial security systems, it has been noticed that SCADA systems also face DDoS attacks. A recent survey estimated that the DDoS attacks on SCADA systems have doubled in the security space. For example, in 2017, the BBC website faced the largest DDoS attack in the history, in which, the network bandwidth was overloaded to around 602 Gbps that forced BBC to shut down the network. Furthermore, a network operator in Asia faced a DDoS attack in 2016, in which, around 334 Gbps network bandwidth was consumed. Protection against DDoS attacks is not an antidote, but a logical precaution, which is important for any organization that has business dependency on the internet services.
ENCRYPTION
A strong network architecture is needed to secure, monitor, and control the industrial processes in industries, such as oil and gas, and water plants. The increase in highly interconnected networks between control networks and public networks result in exposure to various cyber threats and vulnerabilities within organizations. Encrypting the ICS helps mitigate common attacks, such as data theft and DDoS attacks, and provides high reliability, performance, and availability of these networks on-demand. In 2017, Check Point Software Technologies and RAD formed a partnership to offer an end-to-end cybersecurity software solution using SCADA equipment. Market players such as Nozomi Networks, Fortinet, Alutech, and Thales offer SCADA encryption solutions to industrial control networks and other critical infrastructures.
FIREWALL
The integration of control system networks with corporate networks has increased cybersecurity vulnerabilities. Firewalls in industrial systems are mostly deployed between the industrial control network and the corporate network. These vulnerabilities expose various levels of industrial network architecture to a variety of cyber threats, including viruses, worms, and malware. Firewalls are the devices or systems that control and manage the flow of network traffic, which has any kind of disturbance in security postures. They also help protect sensitive resources of an enterprise network from non-essential traffic and unauthorized users, and other compromised networks. Properly configured firewalls could prohibit unnecessary data from passing between networks, such as control and corporate networks. A Next- Generation Firewall (NGFW) is an integrated network platform that comprises all the capabilities of the traditional firewall, with the addition of extra functionalities, such as DPI, IPS, Secure Sockets Layer (SSL) and Secure Shell (SSH) interception, antivirus inspection, and Virtual Private Network (VPN). The firewall solution industry is facing stiff competition from one-stop security solutions, such as UTM, NGFW, and virtual firewalls. In 2016, Fortinet launched various firewall products, such as FortiWeb 4000E, 3000E Web Application Firewalls, and FortiGate-600D Enterprise Firewall, and also formed partnerships with Attivo Networks and BT to enhance its firewall products. Other market players such as McAfee, Check Point Software Technologies, and Bayshore Networks offer effective and in-depth defense firewall solutions for the ICS and SCADA networks.
IDENTITY AND ACCESS MANAGEMENT
IAM is an essential security solution for resource-driven environments, such as ICS/SCADA, smart homes, personal health monitoring, or the automotive industry. To better guard the control systems, automation, transmission, and distribution, the companies are required to be able to control access to their network resources. Examples of network resources include ICS, equipment, buildings, and IT, all of which have unique challenges that may be technical or political. IAM systems for these assets often exist in silos, and employees who manage these systems lack methods to effectively coordinate access to the devices and facilities in these silos, which may result in various security risks. To mitigate such risks, industrial enterprises must proactively protect and monitor privileged accounts that enable access to the industrial environments. This is the reason for which IAM has the fastest growth rate in the Industrial Control Systems security solutions market. IAM reduces the risk of unauthorized access to critical systems, by securing and controlling access to privileged accounts. Many companies such as CyberArk and Symantec have implemented steps to provide secure remote access, while also decreasing the risk attached with malware.
INTRUSION DETECTION SYSTEM/INTRUSION PREVENTION SYSTEM
Modern industrial systems have started integrating the control system networks with the corporate enterprise networks. IDS/IPS technologies are used to monitor malicious behaviors and detect suspicious patterns that can compromise the security of a computer system/network. IDS/IPS tools, such as Snort and Office of State Security and Emergency and Coordination (OSSEC) provide protection against potential security threats. ICS and SCADA systems need to integrate these technologies to defend against the growing threat landscape. Information from systems or from networks is gathered, from which the possible security breaches are identified. The types of IDS/IPS systems are Network-Based Intrusion Detection System/Network-Based Intrusion Prevention System (NIDS/NIPS) and Host-Based Intrusion Detection System/Host-Based Intrusion Prevention System (HIDS/HIPS). The host-based types monitor the network, such as servers and workstations, whereas the network-based types monitor the traffic between the network and network components. Among the leading players, Fortinet entered into an agreement with BT in 2017 to provide intrusion prevention to their customers. Solution providers such as Check Point Software Technologies, Cisco, and FireEye, also offer IDS/IPS solutions for securing the ICS and SCADA networks.
SECURITY AND VULNERABILITY MANAGEMENT
Security and vulnerability management is a proactive approach to secure sensitive data by eliminating the weaknesses of the network security, which include contingent cyber threats such as dormant malware attack and other advanced invasion techniques. The process includes the checking and identification of risks along with mitigation and patching of unwanted software programs. Businesses rely on the solution to quickly assess and prioritize the vulnerabilities, along with scanning the network asset information, security configuration, and threat intelligence. This segment covers the products that scan devices such as servers and workstations or applications/software to uncover known as well as unknown vulnerabilities. Enterprises extensively adopt security and vulnerability management solutions across industry verticals, such as retail, BFSI, government and defense, manufacturing, healthcare, energy and utilities, and retail to safeguard their digital assets. The applications, endpoints, and networks of organizations are the most common targets of cybercriminals to penetrate the network and access confidential data. Security and vulnerability management is deployed in the IT infrastructure of both SMEs and large organizations. Moreover, organizations implement security and vulnerability management to categorize the level of security required to improve their security posture.
The contributing factors for the market growth of the solution are the increasing use of diverse operating systems, increasing volume of data, rapid adoption of Bring Your Own Device (BYOD) trend, growing number of mobile devices at workplace, and cloud computing. These expanding security threats are prompting businesses to adopt frequent assessment and monitoring of vulnerabilities in the systems.
SECURITY CONFIGURATION MANAGEMENT
The industrial network security relies heavily on asset discovery, which lays emphasis on keeping a track of authorized devices. Security configuration management is extremely important for integrating IT and OT security and configuration. It brings together practices such as vulnerability assessment, automated remediation, and configuration assessment. Security configuration management helps enterprises in being compliant with PCI DSS, HIPAA, and SOX and following standards such as NIST and ISO 27001. Some of the significant security controls and plans defined in the NIST specified SP 800-53 include configuration management policy and procedures, baseline configuration, configuration change controls, security impact analysis, security and configuration settings, and management plans. Some of the significant benefits include reduced IT management overhead; streamlined IT operations which include network, OS, endpoint, and application management; automated security checks for firewall, patches, and logs; compliance management; and data protection.
SECURITY INFORMATION AND EVENT MANAGEMENT
The security of industrial systems has increased in the recent years due to rise in the number of cyber-attacks (Stuxnet 2010, Sasser 2004, and SoBig 2003). SIEM is a security approach that provides a holistic view of an organization’s IT security. SIEM provides a centralized view of real-time analysis of security alerts that are generated from network devices (switches, controllers, HMIs, and firewalls), and applications. It combines the necessary supporting technologies, such as vulnerability assessment and IDS that are appropriate for the industrial applications. Companies such as McAfee, CyberArk, and Siemens have collaborated with other companies to enhance the SIEM solutions for industrial systems. Other leading security vendors, such as Enterasys, Cassidian, AccelOps, and NitroSecurity also offer SIEM solutions for smart grid control networks and other critical infrastructures.
WHITELISTING
Whitelisting refers to specifying a list of programs that are allowed to run on a computer system. Applications have to be explicitly approved by the administrators as legitimate before they can run on an enterprise or industrial system. The whitelisting methodology assigns a hash value to the software or application. If the hash in the whitelist matches the hash of the software program, then the program is allowed to run. Whitelisting is an important methodology to prevent zero-day attacks. Important steps in implementing whitelisting include identifying files that need to be monitored, programming decisions by either raising a red flag or blocking the software program and providing security patches and security updates.
Best Industrial Control Systems Security Solutions 2022
360Quadrant For Industrial Control Systems Security Solutions, Q2 2022
The 20 Companies That Matter Most And How They Stack Up
599,864 professionals have used our research since 2010
Sophos Intercept X provides a comprehensive defense-in-depth approach to endpoint protection rather than depending on one primary security technique. The power of the plus is a combination of leading foundational and modern next-gen techniques. Intercept X integrates the industry’s top-rated malware detection and exploit protection with built-in endpoint detection and response (EDR).



