Application control is a security approach to block unwanted and unauthorized applications from being executed on enterprise endpoints to protect data against potential risks. The software safeguards various business-critical endpoints, such as desktops, laptops, smartphones, tablets, Point-of-Sale (POS) systems, virtual machines, and other fixed function devices, and protect them from threats such as Advanced Persistent Threats (APTs), zero-day malwares, and targeted attacks. With the proper application control solution, an organization can greatly reduce the risk of losing critical data while ensuring data integrity and improved business continuity.
Top 10 Application Control Software
These are the organizations that offer established and reliable digital transformation solutions and services and also are strategically and geographically well placed. Some of the major players are:
- Symantec Corporation
- Intel Security
- Trend Micro Incorporated
- Check Point Software Technologies
- Digital Guardian
- CyberArk
- Heat Software USA
- Carbon Black
- Ivanti Appense
- Arellia
Top Application Control Software Features
As the nature of cyber-threats is becoming sophisticated and complex day by day, the traditional security solutions such as antivirus, antimalware, and firewall have proved ineffective to defend network and endpoints against advanced threats. The convergence of IT and cyber security has changed the security market dynamics with more and more applications integrating with endpoints. It has become very important for businesses to properly assess the software prior to choosing one. Below mentioned are of some of the features that businesses can consider prior to choosing an ideal Application Control Software:
- Active Whitelist
- Progressive Memory Protection
- Knowledge Acquisition
- Reputation Based Execution
- Centralized Management
- Malware Protection
- Total Endpoint Security
- Improved Inventory Management
Top Application Control Use Cases
Using a general set of security standards for all devices doesn’t make much sense. So it is critical for businesses to spend some time in summarizing the main use models of these devices and defining some standard ‘profiles for which they can then design apt security controls. Belo mentioned are some of the important use cases:
- Fixed Function Devices
- Servers
- General Purpose Devices
- OS Lockdown
As the nature of cyber-threats is becoming sophisticated and complex day by day, the traditional security solutions such as antivirus, antimalware, and firewall have proved ineffective to defend network and endpoints against advanced threats. The convergence of IT and cyber security has changed the security market dynamics with more and more applications integrating with endpoints. This in turn is driving the need for deploying application control solutions in small, medium, and large enterprises.
Symantec Corporation, Intel Security (McAfee), and Trend Micro, Inc. lead in the application control market and are recognized as Visionary Leaders. They have strong product portfolio and robust business strategy to achieve continued growth.
HEAT Software USA, Inc. (Lumension Security, Inc.) is identified as a Dynamic player in the market. It is strong in business strategy and has made recent partnerships with other key vendors for inorganic growth. It has the potential to broaden its product portfolio to compete with other key market players.
CyberArk Software Ltd., Digital Guardian, and Carbon Black, Inc. are recognized as Innovators in the application control market. They have innovative products and the potential to build strong strategies for their business growth to be at par with the Vanguards.
Check Point Software Technologies Ltd., LANDESK Software (AppSense), and Thycotic (Arellia) are recognized as Emerging players in the application control market. They have the potential to build on strong product portfolio and business strategy to compete in the market with the Vanguards and Innovators.
Application Control Software
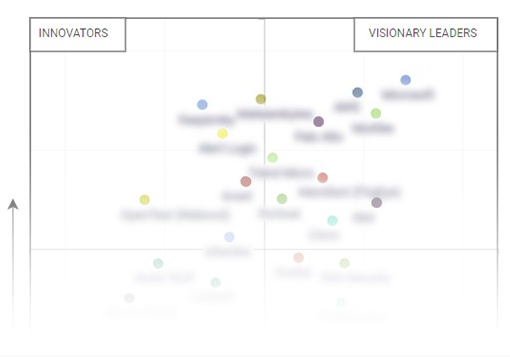
360Quadrant For Application Control Software, Q2 2022
The 20 Companies That Matter Most And How They Stack Up
599,864 professionals have used our research since 2010
Check Point is a leading B2B and B2C IT security service provider. The company offers complete security solutions from internet security, network security, cloud security, device security to data and endpoint security. The company offers reliable 5th generation cybersecurity architecture–Check Point Infinity–designed to protect the enterprises from highly dangerous cyberattacks like ransomware, in the configuration of security software, hardware, and services to all sizes of organizations and consumers. The other software solutions offered by the company are Check Point–Firewall and Check Point–EndPoint.



